Base information
CTF name: Nixu Challenge
Challenge name: ACME phone
Challenge description: The customer (ACME) has delivered an iPhone backup that needs to be investigated. They want to know the whereabouts of one of their employees. It’s broken, they said. It’s impossible to access, they said. Are you an elite forensics investigator? Can you rock?
Target: iPhone_backup.zip
Challenge category: Forensics
Challenge points: 200
Year: 2020
Solution
The given backup file is encrypted iPhone backup. I tried ~5
different forensics software until I was able to find one, being
able to handle the backup correctly. To my surprise, the password
for encryption was password, my second guess. The
software had very limited functionalities of free tier, so I had to
keep looking. Finally, I found open source iTunes
Backup Explorer from GitHub, that was able to decrypt the data
and export it to my filesystem.
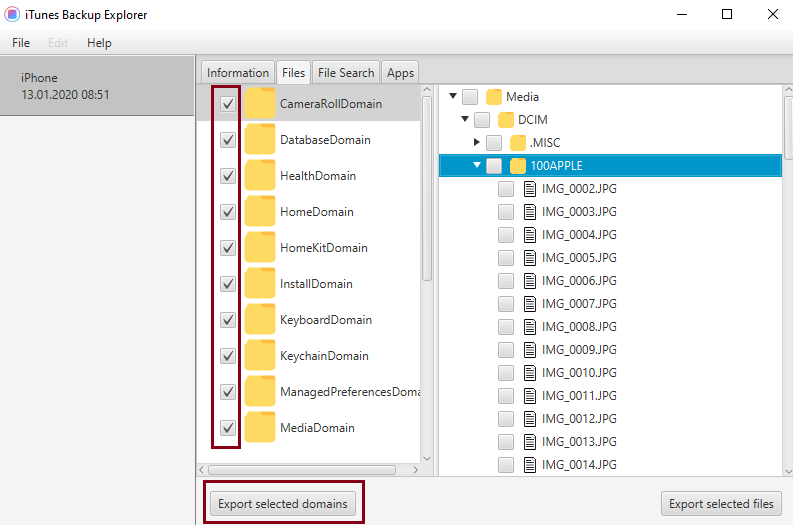
- Select all data and export it.
After decryption, I was able to use iLEAP, familiar tool from GenZ 2022 mobile challenges.
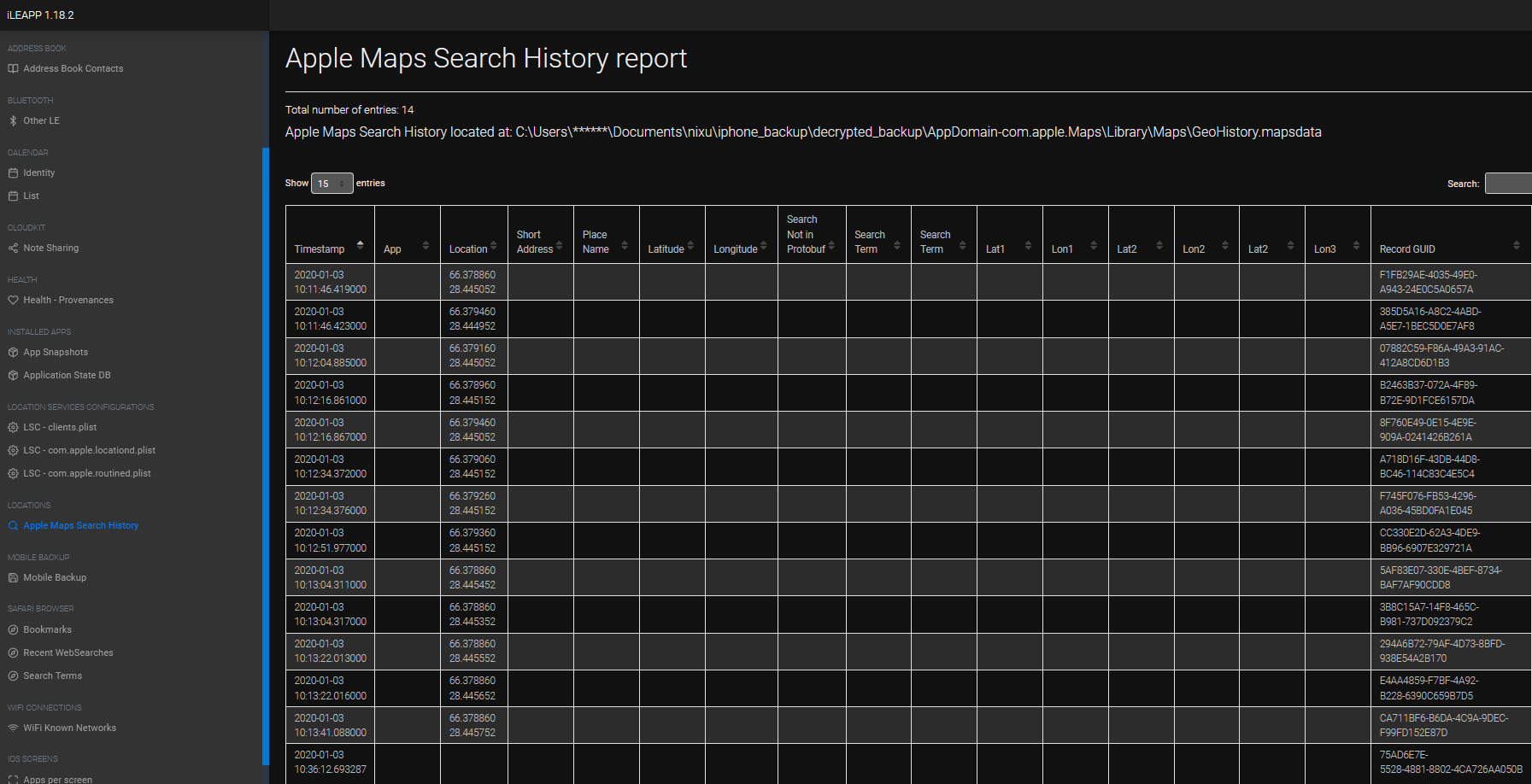
I found one interesting value from the Apple Maps Search History report
{
'1': 1,
'2': 0,
'4': 43200,
'5': 0,
'6': 1,
'8': {
'1': {
'1': 51,
'11': {
'1': {
'12': 1111960942
},
'3': b'\x1b\\tn=address\\ 97895 \x1b\\tn=normal\\'
},
'19': 2
}
},
'9': [
b'apple',
b'revgeo',
b'FI'
],
'10': 10,
'11': {
'2': b'placeRequest=ChAKDmNvbS5hcHBsZS5NYXBzOAFCPwo9GhM2Ni4zNzg4NjAJMjguNDQ1NjUyIiYKJCnISTDLqIxQQDGQSBBJq+M7QDkaa++bzp5QQEF4t3dyGfk8QA=='
},
'12': 2,
'2000': 4738314196906571616
},Following base64 encoded value seems interesting:
ChAKDmNvbS5hcHBsZS5NYXBzOAFCPwo9GhM2Ni4zNzg4NjAJMjguNDQ1NjUyIiYKJCnISTDLqIxQQDGQSBBJq+M7QDkaa++bzp5QQEF4t3dyGfk8QA==
and base64 decoded value is:
.
.com.apple.Maps8.B?
=..66.378860 28.445652"&
$)ÈI0˨[email protected]«ã;@9.kï.Î.P@Ax·wr.ù<@There seems to be similar coordinates than previously and some encoded message witch I assume is the flag.
I tried to encode it with several recipes in CyberChef including xor, ROT and different text encodings.
Conclusion
Hardest part was finding right software