Base information
CTF name: Nixu Challenge
Challenge name: vault
Challenge description: Can you guessss the passssword? (Nah, I lied, no guessing is needed.)
Target: vault (python 2.7 byte-compiled)
Challenge category: Scripting
Challenge points: 100
Year: 2018
Solution
First I run strings command against vault. I found interesting string, but I was not able to get anything from that.
7d650dee190a3e1770c211fad8356996f873367e76008f30bdb932f2820b809e
Then I put the file in reversing software Cutter. I decided to start writing the
software back to its original form and check if code I had written
looks similar when converted to python byte-code using
dis library.
Then I realized I need to use Python version 2.7 for better
results. At the end of reversing check() funktion, I
realized the correct password. I still wanted to fully reverse the
vault program.
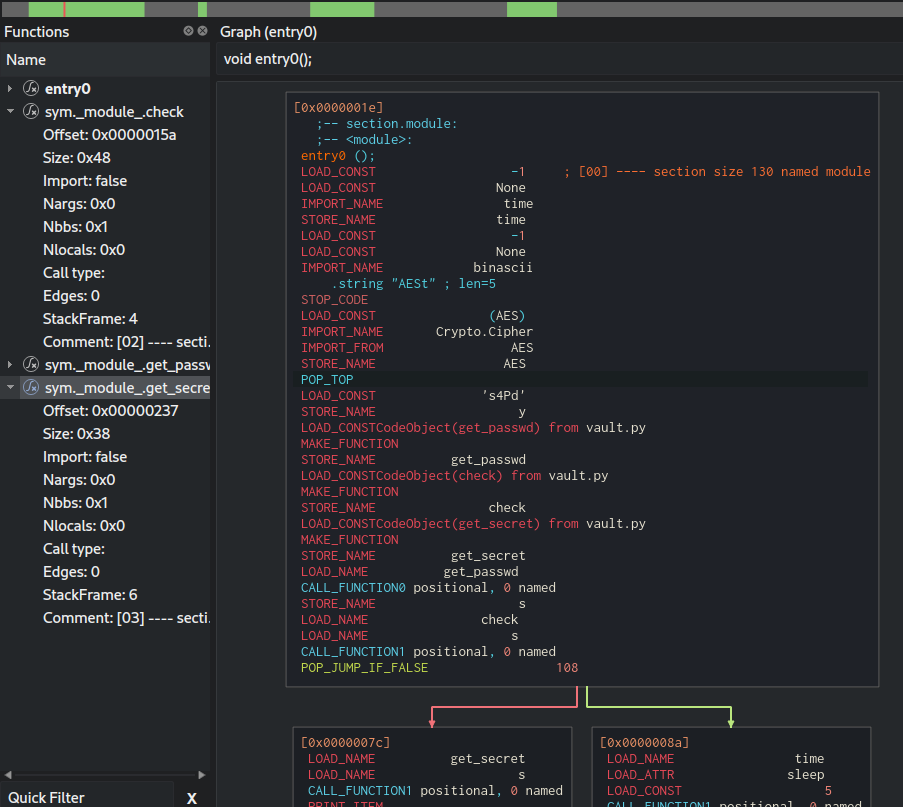
- Screenshot of Cutter, showing the byte-code of vault.
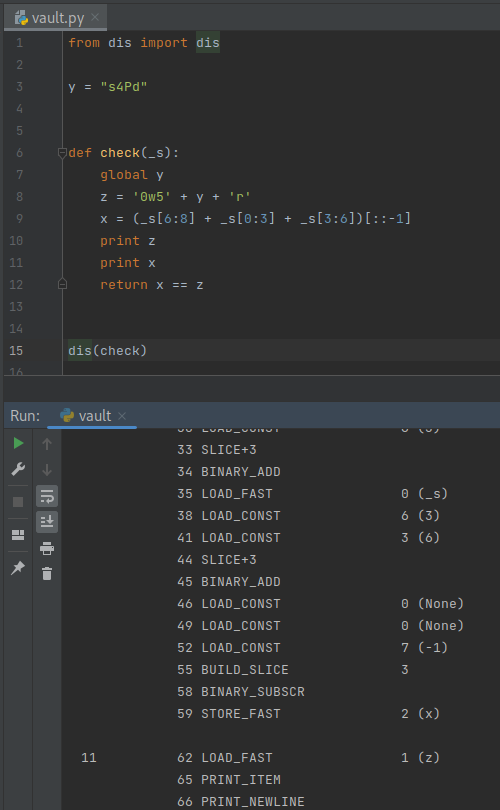
- Screenshot of code editor printing my code in byte-code.
Reverse Engineered vault.py
import time
import binascii
from Crypto.Cipher import AES
y = "s4Pd"
def get_passwd():
return raw_input('Password: ')
def check(_s):
global y
z = '0w5' + y + 'r'
x = (_s[6:8] + _s[0:3] + _s[3:6])[::-1]
return x == z
def get_secret(k):
secret = binascii.unhexlify('7d650dee190a3e1770c211fad8356996f873367e76008f30bdb932f2820b809e')
aes = AES.new(k * 2, AES.MODE_CBC, b'thisIsNotTheFlag')
return aes.decrypt(secret)
s = get_passwd()
if check(s):
print(get_secret(s))
else:
time.sleep(5)
print('Invalid password!')I leave the correct password for you to find out :)
Conclusion
This Challenge was fairly similar to one of GenZ 2022 challenges,
but still very good training for revere engineering. There is
probably some software to automate Python byte-code reversing.
Probably the hardest part was reversing get_secret()
function, it took me a while to realize witch variables belong to
where. Overall nice challenge.